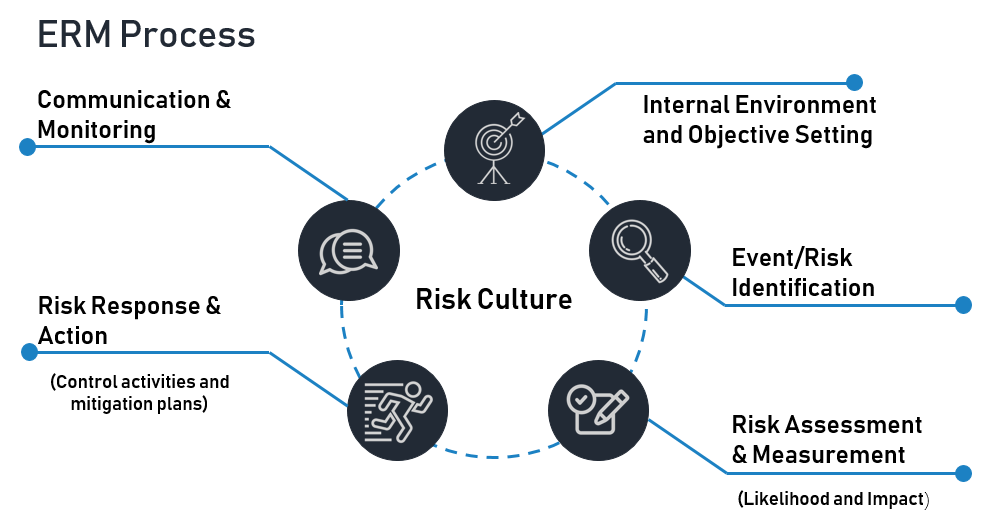
Enterprise Risk Process and Management
Our approach to assessing enterprise risk delivers an evidence-based analysis of your organization’s current cyber risk posture, a prioritized risk remediation list, and the data management for making informed decisions on cyber risk reduction investments.
Our reports highlight the assets, business processes, and technologies representing the greatest risk, treatment options, and anticipated residual risk once items are remediated. This approach enables you to improve your overall cyber risk posture and enhance your cyber resilience.
Our Information Cyber Security Professionals will:
- 1.) Identify the assets critical to your organization’s ability to deliver services.
- 2.) Analyze the protective and detective controls supporting the organization.
- 3.) Define the cyber risk, potential for loss, disruption, exposure, or corruption of those assets.
- 4.) Describe your organization’s risk posture.
- 5.) Develop prioritized recommendations and a roadmap for risk remediation.
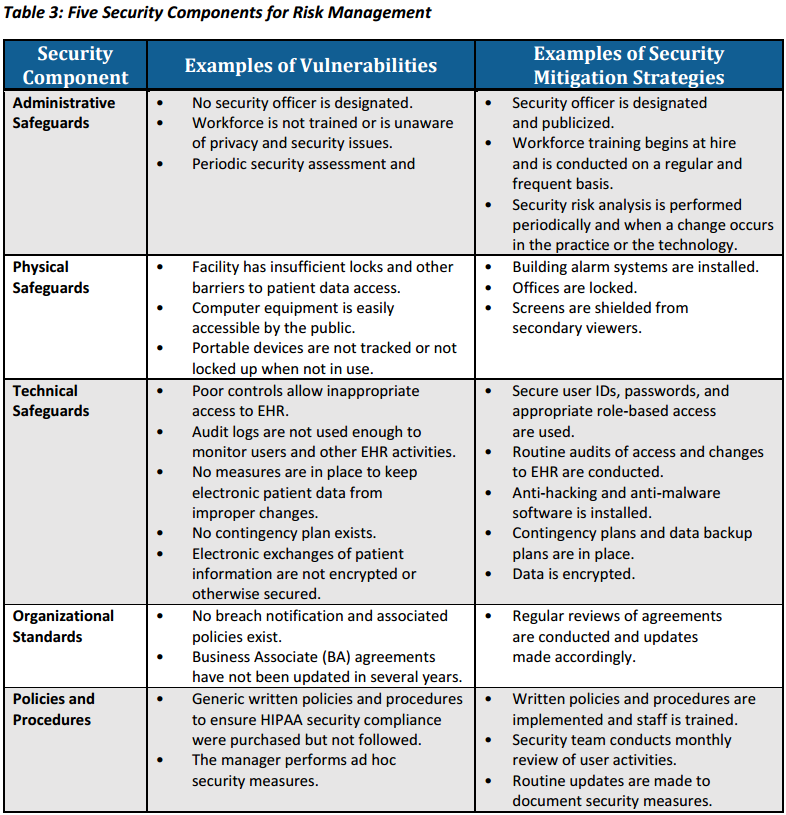
HIPAA-Risk Management
Difference between Vulnerability Testing and Risk Assessment
Risk assessments and vulnerability assessments might seem like the same thing on the surface, but these two concepts are indeed distinct. IT Risks are potential threats or hazards related to an organization’s use of technology, processes and procedures. Vulnerabilities, on the other hand, are weaknesses in the technology that can potentially be exploited.
Risk assessments focus on identifying potential threats associated with a new project or undertaking. The idea is to identify areas of incomplete knowledge, fill in those gaps, and then take steps to mitigate the potential threats.
Vulnerability assessments focus on identifying existing weaknesses in assets or control that malicious actors can exploit and cause harm. Performing a vulnerability assessment allows an organization to identify vulnerabilities and security gaps and then take measures to eliminate them.
In essence, risk assessment involves looking outside of an organization to determine what threats exist that could potentially lead to problems, while vulnerability assessment involves looking inside the organization for structural flaws and weaknesses. The former evaluates which armies might approach the castle gates while the latter checks the locks on the doors.